Ransomware attacks have evolved into one of the leading threats to a business that more often than not, comes with significant financial ramifications.
In fact, the average cost of an attack can reach into the millions of dollars, and according to Cybersecurity Ventures, the global annual cost of cybercrime is predicted to reach $8 trillion USD this year.
Compounding this is the rising cost of damages resulting from cybercrime, which is expected to reach $10.5 trillion by 2025.
It takes an average of 277 days for security teams to identify and contain a data breach, according to “Cost of a Data Breach 2022,” a report released by IBM and Ponemon Institute. Cybercriminals are becoming more sophisticated in their methods and their effects, even targeting backup systems to prevent data restoration following an attack.
It’s crucial to recognize the significant financial impact that ransomware attacks can have on an organization, and to put in place tested cybersecurity strategies that can help prevent and mitigate these risks.
However, no matter what prevention strategies you have in place, sophisticated cyber thieves are continually proving to be able to get around those measures.
So does that mean you should throw up your hands, and do nothing?
Of course not. It means that you have to ensure that you can recover fully from any cyber attack. In this blog, we will show you the most common reasons why recovery efforts fail, and then give you some actionable solutions you can implement within your business.
Factors Contributing to Failed Ransomware Recovery
Recovery from ransomware can be a difficult and complex process, and unfortunately, there are several reasons why recovery efforts may fail.
Here are the top reasons:
- No data back up or infrequent backups
- Incomplete or corrupted backups
- Insufficient testing of backup and restoration process
- Delayed response to an attack
- Inadequate cybersecurity measures
We’ll go into depth on these issues in this blog, but also checkout the webinar “How to Create a 360° Ransomware Recovery Plan” to understand more about why you this is a critical part of your data protection strategy.
You don’t have a data backup or backups are infrequent…
Ransomware typically encrypts a victim’s files, making them inaccessible. If there is no backup of the encrypted data, it can be difficult or impossible to recover the files. Having a comprehensive backup strategy to address this is critical to ensure that data can be restored in the event of a ransomware attack.
How frequently do you run backups? If you were attacked at the very last moment before your next backup ran, could your business survive?
If the answer to that is no, it is essential to increase the frequency of your backups.
Luckily, modern backup software solutions now provide innovative technologies like block-level incremental (BLI) backups to enable backups throughout the day and reduce data transfer. However, keep in mind that even if your critical systems can be restored, non-mission-critical data may still be locked behind a ransom demand.
Increasing backup frequency and scope is an effective strategy, however keep in mind that it can put a strain on backup infrastructure. The random nature of frequent backups can be a challenge for backup storage hardware to keep up with.
Here’s what you can do if this is your problem:
Now you know that you need to set up your backup strategy to be frequent enough to ensure your business will survive — but you also need to make sure that this will not place undue strain on the backup infrastructure…
Here’s what you can do:
Incorporate the power of flash storage for high-speed backup and recovery operations and slower, denser storage for long-term data retention. Through the power of optimized data placement, you’ll be able to achieve the perfect balance of performance and cost-effectiveness for your organization’s specific data retention and recovery needs.
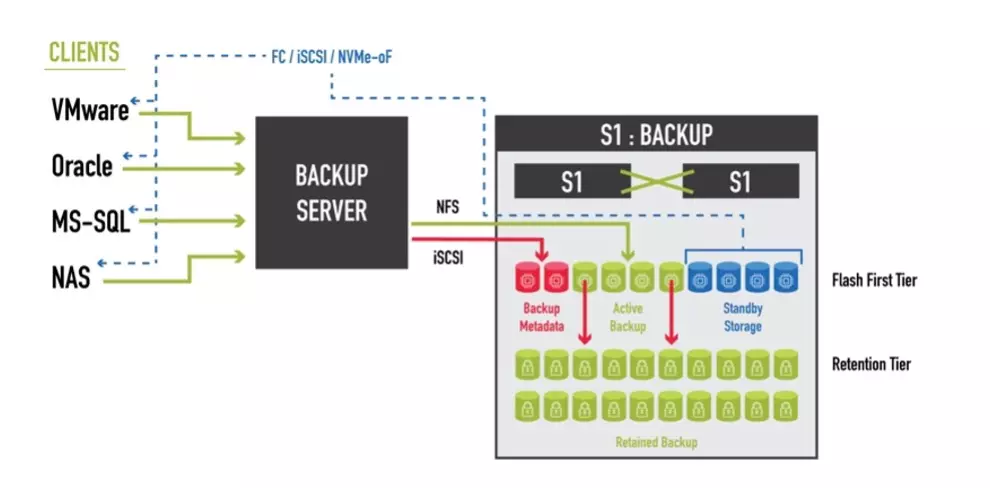
Incomplete or corrupted backups:
Although backups are an essential component of ransomware recovery, they may not always be sufficient. Incomplete or corrupted backups can make data restoration a challenging and time-consuming task. Cybercriminals understand this and may target backup data to disable the victim’s ability to recover data, effectively holding the data hostage until the ransom is paid.
The 3-2-1 data protection model is a widely recognized approach for securing and safeguarding data.
This model says you should have 3 copies of data, stored on 2 different types of media, with 1 copy stored offsite. This ensures data redundancy, which can help prevent data loss in case of hardware failures or disasters.
While the 3-2-1 model is a solid starting point, it is not always sufficient to provide complete data protection. Cyberattacks such as ransomware can circumvent these safeguards by encrypting or destroying all available copies of data, including offsite backups. In these scenarios, organizations require more advanced data protection, including immutable backups that cannot be changed or deleted by ransomware, early detection mechanisms to detect threats before they cause damage, and rapid data recovery techniques that can help reduce downtime and minimize the impact of an attack.
Here’s what you can do if this is your problem:
Let’s take a look at Air-Gap Backups. An air-gap backup is a backup method in which the backup data is physically isolated from the network or computer system being backed up. The term “air-gap” refers to the complete lack of connectivity between the backup data and the source system.
This method is considered one of the most secure forms of backup as it is extremely difficult for malware or cybercriminals to access or manipulate the data.
There are different types of air gap backups, including:
- Offline backups: This involves storing backup data on physical media, such as tapes, which are then physically disconnected from the network or computer system.
- Offline and offsite backups: This involves creating offline backups and then storing them offsite in a secure location.
- Immutable backups: This type of backup uses write-once-read-many (WORM) media or data storage systems that prevent any further changes or modifications to the data once it has been written. This can also be achieved with immutable snapshots where the data is written and once the snapshot occurs the data that the snapshot is protecting can not be modified. With StorONE the snapshot can not be mounted and the data can not be modified. Restoration from the snapshot is performed in minutes then the restored data can be mounted and used while keeping the snapshot immutable.
We like the 3-2-1 data protection model paired with immutable, air-gapped backups, and early detection mechanisms. This is a comprehensive strategy to significantly reduce the threat of increasingly sophisticated cyberattacks.
Insufficient testing of backup and restoration processes:
Want to ensure your organization can recover from a ransomware attack and avoid falling victim to extortion demands? Then, testing specific to a ransomware attack is critical.
In a natural disaster, for example, the primary data center is usually offline or destroyed, but the DR site has a clean copy of data that can be leveraged to restore operations. However, ransomware attacks can be much more insidious. The data center may still appear to be functional, but the data has been corrupted, and the backup copies at the DR site may also be unusable. To make matters worse, the attack may still be underway, adding pressure to the restoration process. End-users are typically waiting impatiently to regain access to their applications, so time is of the essence, and the temptation to pay the ransom can be overwhelming.
This is why testing for ransomware attack scenarios is so important. By simulating a ransomware attack, organizations can identify potential weaknesses in their recovery strategy and ensure they can quickly restore operations and avoid paying ransoms.
Some victims of ransomware choose to pay the ransom to obtain the decryption key. However, there is no guarantee that the attacker will provide the decryption key, and paying the ransom may encourage further attacks.
Even during recovery, malware-trigger files may still be present on production storage, poised to re-infect any recovery efforts. Unfortunately, many organizations lack a solution to this problem, and industry analysts have questioned the cost-effectiveness of implementing an isolated recovery environment. For most organizations, it may not be practical to have a system sitting idle in the data center solely for ransomware recovery purposes.
If you haven’t tested for a ransomware attack… here’s what to do:
Look for a backup storage target that can build on the instant recovery performance described above to deliver standby storage. A backup storage target with this capability is highly available and has enterprise storage features like snapshots and replications. There are reasonsbeyond ransomware recovery for standby storage, but its ability to see an organization through an attack is invaluable. Most importantly, the standby storage capability requires only a minimal addition in backup storage costs.
Test, Test, Test
Here are a few examples of how to test ransomware recovery scenarios.
- Conduct tabletop exercises: A tabletop exercise is a simulation that tests the effectiveness of a ransomware recovery plan. During the exercise, team members can role-play different scenarios to identify potential gaps in the plan.
- Run a virtual recovery test: A virtual recovery test is a test that simulates a ransomware attack in a virtual environment. The virtual environment can help identify any potential issues with the recovery process, such as the time it takes to restore data or potential conflicts between different systems.
- Test backups: It’s essential to test backups regularly to ensure they can be restored in case of a ransomware attack. Testing backups can help identify any issues with the backup process, such as data corruption or incomplete backups.
- Test your security controls: To prevent a ransomware attack from happening in the first place, it’s important to test your security controls regularly. Penetration testing and vulnerability assessments can help identify any weaknesses in your security controls that could be exploited by attackers.
By conducting these types of tests, organizations can identify any gaps in their ransomware recovery strategy and take the necessary steps to improve their readiness for a potential attack.
Delayed Response to a Ransomware Attack:
Delaying the response to a ransomware attack can make it more difficult to recover data. Ransomware often spreads quickly and can infect multiple systems, so a prompt response is essential to contain the attack and minimize the damage.
The impact of a ransomware attack can be severe, with an average downtime of 21 days. Even if you choose to pay the ransom, it could still take several additional days to receive the decryption key and undo the damage caused by the encryption. Furthermore, the data decryption process can take several days to weeks, and inspecting the data for any lingering malware that could re-infect the system can also take several days. It’s clear that recovering from a ransomware attack is a complex and time-consuming process that requires careful planning and execution.
One of the biggest obstacles that can lead organizations to abandon their ransomware recovery efforts is the time it takes to restore data. Whether it’s identifying a known good copy of the data or instantiating it for user access, this process can take significant time. According to Sophos’ “The State of Ransomware 2023” survey, average recovery time for a ransomware attack is over a month. While paying the ransom may seem like an appealing option for quick data recovery, only 4% of organizations that paid the ransom were able to recover all of their data. Although modern backup applications offer features like instant recovery to speed up recovery time, if your applications require all-flash or hybrid performance, instant recovery to a hard-drive-only backup storage target may not be well received due to performance degradation caused by additional overhead.
How can you act quickly?
When searching for a backup storage solution, prioritize finding one that can provide production-class performance. By intelligently leveraging the flash tier, as previously mentioned, a backup storage target can reallocate capacity to ensure that instantly recovered data performs on par with production.
Inadequate Cybersecurity Measures:
Inadequate cybersecurity measures, such as outdated software, weak passwords, and lack of employee training, lack of Endpoint Detection and Response (EDR) tools, can make an organization more vulnerable to ransomware attacks. Without effective cybersecurity measures in place, recovery efforts may fail.
Prevention is key in the fight against ransomware. The human element poses the greatest threat vector, accounting for 82% of data breaches. Human error, particularly in the form of phishing attacks and stolen credentials, is a primary driver of these breaches. Phishing attacks, usually executed via email, lure unsuspecting users into clicking on a link or sharing information that can then be exploited by malicious actors. By following these best practices, you can help to protect your business from ransomware attacks and minimize the impact of a potential breach.
Tips to follow best practices:
- Keep remote desktop services like RDP off public networks, and if necessary, use robust passwords to secure them.
- Always install available patches for commercial VPN solutions that provide access for remote employees and gateways on your network.
- Prioritize lateral movement and data exfiltration detection in your defense strategy. Monitor outgoing traffic for any signs of cybercriminal activity.
- Make data backup a routine practice and ensure quick access to backups in emergency situations.
- Consider using advanced security solutions like CrowdStrike, SentinelOne, and Microsoft Defender service to detect and stop ransomware attacks before they reach their final goal.
- Stay informed of the latest Threat Intelligence information to stay on top of the actual TTPs used by threat actors.
- Immutability in snapshots is crucial to prevent accidental or deliberate deletion. An override may be necessary in case of snapshot growth risks, but it should require additional validation and authorization through a trusted route that involves IT team members in contact with the vendor to prevent any spoofing attempts by a hacker





